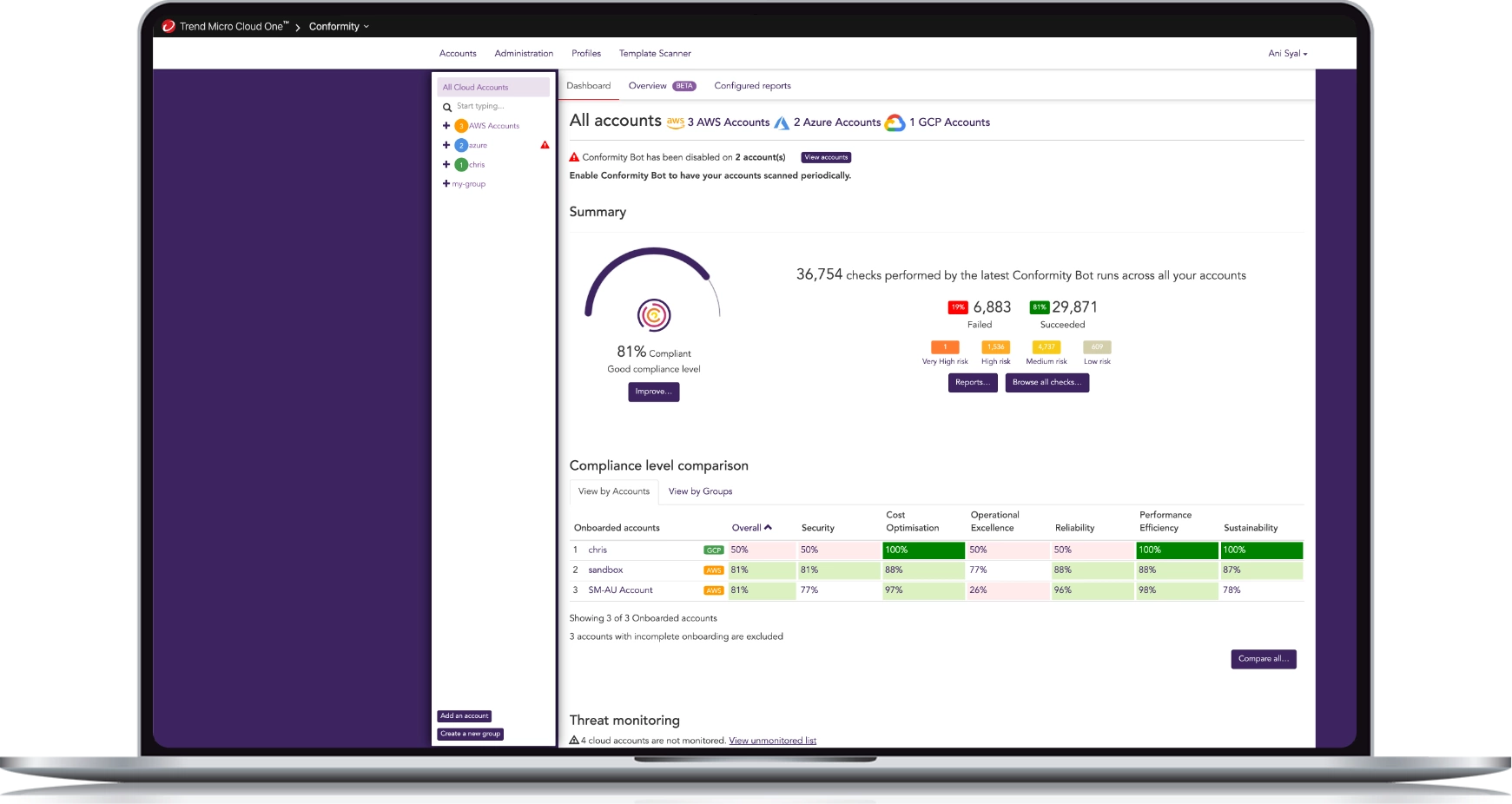
Comprehensive visibility and auto-remediation
Visibility and monitoring of your cloud infrastructure from one multi-cloud dashboard. Auto-check against nearly 1,000 cloud service configurations from AWS, Microsoft® Azure®, and Google Cloud Platform.
View risk status, resolve violations, and improve security and compliance posture with accessible guides or auto-remediation.

Automated security and compliance checks
Run scans against numerous best-practice checks – SOC2, ISO 27001, NIST, CIS, GDPR, PCI DSS, HIPAA, AWS, Azure Well-Architected Frameworks, and CIS Microsoft Azure Foundations Security Benchmark.
Leverage standardized or custom reports and audit infrastructure with nearly endless filters.

Enable developers
Infrastructure as code (IaC) scanning ensures secure and compliant templates are deployed according to best practices.
Integrate into your CI/CD pipeline with powerful APIs with alerts on configuration changes for immediate action.
Connect to third-party providers – Slack®, Jira®, Zendesk®, PagerDuty®, Microsoft® Teams, and more.
KEY USE CASES
How Conformity helps cloud builders
I have a cloud service storing sensitive data that is publicly accessible. How can I quickly change permissions?
Auto-remediation automatically addresses high-risk violations, such as open storage access, which can prevent malicious actors from accessing sensitive data.
My team is rapidly growing and making the most of cloud computing. How do I keep track of all their cloud services?
A multi-cloud view of your AWS and Azure infrastructure lets you see your risk status and quickly remediate high-risk violations.
How do I keep my infrastructure compliant with GDPR and prove compliance?
Stay GDPR compliant with regular infrastructure checks directly applicable to the regulation and schedule exportable reports required for audits.
I need pre-built and custom reports on the security and compliance status of our cloud security posture. Is this possible?
Run preconfigured or customized reports by any filter. The endless filter combinations enable you to exhaustively audit your infrastructure.
How do I ensure the IaC templates we create to deploy cloud infrastructure are reliable, secure, and compliant before production?
CloudFormation Template Scanning lets you shift security and compliance checking left, improving your code. IaC template scanning checks against hundreds of best practices, so you can innovate worry-free.
I'm concerned about unauthorized access to our cloud services. How do we prevent this from happening?
Automatically ensure IAM policies are enforced with Conformity's many IAM configuration checks.
WHY CONFORMITY
Ensure compliance vs Continuous Compliance Monitoring
Security you can trust
The AWS Well-Architected Framework provides a consistent approach to building cloud architectures that can scale over time. Conformity enables you to fulfill your side of the shared responsibility model with continuous guardrails for building in the cloud.
Ensure compliance
Industry standards and compliance requirements are constantly changing. Benefit from continuous scans against compliance and industry standards in your cloud infrastructure and immediately act on high-risk policy violations.
Follow best practices easily
Our knowledge base is a repository of cloud service configuration guides to best practices and compliance standards.
Conformity automatically scans cloud services against best practices for automated pass or fail checks. Auto-remediation can automatically address other rules.
Real-time monitoring and remediation information expedites cloud migration and DevOps processes, without introducing additional risks.

Free public cloud risk assessment
Are you building a secure and compliant cloud infrastructure? Quickly determine your risk level with our automated security, governance, and compliance cloud risk assessment. Our cloud engineers will run this check for your AWS and Azure cloud environment in a complimentary session.
Trend Cloud One
Get more than a cloud-native application protection platform (CNAPP) with meaningful intelligence for security teams and developers at the right time in the right place. Procure the protection you need the way you want and deploy the way you need.
The protection you need, the way you want. Leverage the power of meaningful intelligence for security teams and developers with a cloud-native application protection platform (CNAPP) that does more.

Forrester Total Economic Impact Study
Discover the projected cost savings and business benefits of Trend Cloud One, our security services platform, which includes File Security and more.
Explore relevant resources
Other Trend Cloud One services
Conformity is part of Trend Cloud One, a security services platform for cloud builders, which includes:

Workload Security
Runtime protection for workloads (virtual, physical, cloud, and containers)

Container Security
Image scanning in your build pipeline

Network Security
Cloud network layer IPS security

File Security
Security for cloud file and object storage services

Open Source Security by Snyk
Visibility and monitoring of open source vulnerabilities and license risks

Cloud Visibility
Inspect your environment in minutes, gain insight into threats, and remediate – all with one platform.
JOIN 500K+ GLOBAL CUSTOMERS
Get started with Conformity